IT network security and cybersecurity are not mutually exclusive. They work together to reduce risk. Network security protects the flow of information and access points. Cybersecurity protects the devices, applications, and data that use the network. However, this isn’t the only reason why network security is important.
| “A layered approach to cybersecurity is always best. This way, even if an attacker gets through one layer of your defenses, you have additional layers to keep you secure.” — Philipp Graves, CEO of Antisyn |
Network security focuses specifically on controlling and monitoring that communication. It protects the flow of information between systems and users by applying controls such as firewalls, intrusion detection and prevention systems, network segmentation, and traffic monitoring. Without this layer of protection, your organization would face additional risks.
These risks are what this article will explore in further detail. We will explain the difference between network security and cybersecurity, why you need both, and the cyber threats that prove you need both.
What’s The Difference Between IT Network Security vs. Cybersecurity?
IT network security is a part of cybersecurity. Cybersecurity encompasses all protections for digital systems and data, while network security specifically safeguards the network and the transmission of data within it.
Here is an overview of the key differences beyond that.
| IT Network Security | Cybersecurity | |
| Primary Goal | Protect the integrity, availability, and confidentiality of the network infrastructure | Protect all digital assets from cyber threats |
| Focus Area | Network hardware, routers, switches, firewalls, network traffic | Data, devices, applications, networks, users |
| Common Threats Addressed | Unauthorized access, network-based attacks (e.g. DDoS), packet sniffing | Malware, ransomware, phishing, insider threats, APTs (advanced persistent threats) |
| Security Tools Used | Firewalls, Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), Virtual Private Networks (VPN) | Antivirus, Endpoint Detection and Response (EDR), Data Loss Prevention (DLP), Identity and Access Management (IAM), cloud security solutions |
| Monitoring Scope | Monitors network traffic and access points | Monitors endpoints, data flow, applications, user behavior, and network traffic |
| Compliance Focus | Often tied to network-related standards (e.g. ISO/IEC 27033) | Broader compliance frameworks (e.g. NIST 800-53/171, HIPAA, PCI DSS, CMMC) |
| Involvement in Incident Response | Detects and helps mitigate network-based attacks | Covers full incident response lifecycle for all types of cyber incidents |
Why Do We Need Network Security If Our Cybersecurity Measures Extend to Our Network?
A cybersecurity program may include some protections that touch your IT network, but network security delivers targeted controls that address risks not fully covered by broader cybersecurity tools.
Cybersecurity solutions often focus on endpoints, user identities, cloud services, and applications. They do not always provide complete visibility or control over the actual traffic moving through your IT network infrastructure.
Attackers frequently use the network as a pathway to reach valuable systems and data. If the network lacks its own security controls, an attacker who gains access to one system can easily move to others.
Once in, they can cause damage undetected. The average dwell time of a persistent threat in an IT network is 51 days in organizations with up to 250 employees.
Specialized network security controls usually come with monitoring systems that allow you to catch such threats before they cause a significant impact. By comparison, many generalized cybersecurity tools focus on known threats and specific systems but do not continuously inspect traffic patterns.
Improve Your Defenses & Decrease IT Issues by 49.8%
7 Key Risks That Emphasize The Importance of IT Network Security
1. Lateral Movement
If an attacker gets control of one device or user account, they often try to move through the network to reach more. Basic cybersecurity tools, such as endpoint protection, can block some attacks on devices, but they do not control traffic between devices inside the network.
Network security measures help stop this type of movement. Network segmentation, internal firewalls, and traffic inspection tools limit the reach of attackers. These tools help contain attacks and prevent them from spreading.
2. Shadow IT Connections
CloudSecureTech points out that one in five employees knows how to bypass their organization’s security rules, allowing them to use shadow IT. This is a problem because shadow IT applications rarely meet the cybersecurity standards that most businesses need. As a result, having shadow IT on your network could open the door to bad actors.
Network security solutions provide visibility into all network traffic, including traffic from unmanaged or unauthorized applications. Network access control (NAC), DNS monitoring, and intrusion detection systems (IDS) can identify and block these connections.
| Learn More About How You Can Maintain Security Using The Right IT Strategy |
3. Device Spoofing
Attackers can impersonate trusted devices or services by spoofing network information such as IP addresses or MAC addresses. Standard endpoint and cloud security tools may not protect you from these attacks and may be fooled into allowing spoofed devices to access your data.
Network security controls such as port security, DHCP snooping, ARP inspection, and DNS security detect and block spoofing attempts. These controls prevent attackers from using impersonation to gain unauthorized access or disrupt network operations.
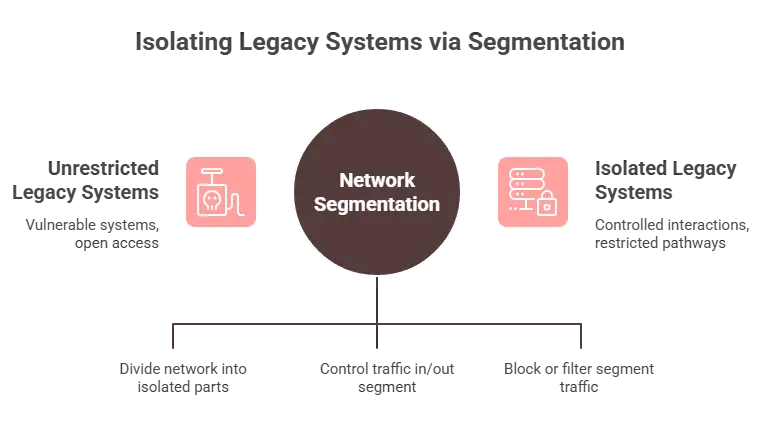
4. Unmonitored Legacy Systems
Some organizations still rely on legacy systems that cannot run modern endpoint protection software. These systems often remain connected to the network and can be easy targets for attackers.
Network security measures protect traffic to and from these legacy systems. Virtual network segmentation, firewalls, and intrusion prevention systems limit the interaction between these systems and the rest of the network.
5. Compromised IoT & OT Devices
Many connected devices, such as cameras, sensors, and machines, lack robust built-in security. These devices also cannot run regular cybersecurity software. If attackers take over these devices, they can use them to compromise your IT systems.
Implementing IT network security means that these devices are separated from critical IT systems. Anomaly detection, deep packet inspection, and NAC help control device behavior and detect attacks.
6. Traffic Manipulation
An employee might move sensitive information or disrupt services using your network, intentionally or not. 95% of data breaches are caused by simple human error, and this is one way in which that can happen. Identity controls and endpoint protections focus on user actions but may not track how users interact with network traffic.
On the other hand, network security tools can see and analyze all network traffic. They can block attempts to move sensitive data outside of your IT network or spot unusual behavior patterns.
7. Malware Propagation
After infecting one device, malware can spread by using the network to reach other devices. Antivirus software may stop infections on individual devices, but it often cannot stop infected traffic from moving through the network.
Network-based malware detection, intrusion prevention systems, and traffic analysis tools help block harmful traffic moving between devices. These tools help contain infections and prevent them from spreading.
| Protect Your IT Network With The Help of Some of Florida’s Leading Cyber Experts | |
| Jacksonville | Orlando |
Reach Out to Antisyn to Enhance Your Network Security
Your IT network plays a critical role in keeping your systems connected and your data secure. As technology evolves, so do the tactics that target these connections. Keeping your network protections current requires both awareness and a proactive approach. Working with an expert partner helps you stay ahead of these risks.
Antisyn helps businesses build that strategy with layered protection for both their network and digital assets. We offer 24/7 monitoring, advanced threat protection, network security tools such as firewalls and VPNs, as well as identity and access controls.
Reach out today to enhance your protection.



